Summary
In November 2024, a critical vulnerability, tracked as CVE-2024-10924, was discovered in the Really Simple Security plugin for WordPress, affecting versions 9.0.0 to 9.1.1.1. With a CVSS score of 9.8, this authentication bypass flaw poses a severe risk to WordPress sites, potentially allowing attackers to gain unauthorized administrative access. This blog post provides a comprehensive overview of CVE-2024-10924, its impact, mitigation steps, and a detailed technical analysis of the vulnerability.
What is CVE-2024-10924?
CVE-2024-10924 is an authentication bypass vulnerability in the Really Simple Security plugin (formerly Really Simple SSL), affecting its Free, Pro, and Pro Multisite versions. The flaw resides in the two-factor authentication (2FA) REST API, specifically due to improper error handling in the check_login_and_get_user function. When 2FA is enabled, unauthenticated attackers can exploit this vulnerability to log in as any user, including administrators, without providing valid credentials.
Affected Versions and Systems
- Plugin: Really Simple Security (Free, Pro, and Pro Multisite)
- Affected Versions: 9.0.0 to 9.1.1.1
- CVSS Score: 9.8 (Critical)
Technical Details
CVE-2024-10924 is a critical authentication bypass vulnerability in the Really Simple Security plugin for WordPress. It affects versions 9.0.0 to 9.1.1.1 and allows unauthenticated attackers to gain access to user accounts, including administrators, by abusing the plugin’s Two-Factor Authentication (2FA) REST API flow.
The vulnerability is introduced due to improper validation of the return value from a critical function (check_login_and_get_user) within the 2FA REST handler. When this function fails to authenticate a user, it returns an error response, but the calling function (skip_onboarding) does not validate that error, and continues to authenticate and redirect the user as if login succeeded.
Root Cause Analysis
The vulnerability originates from a critical flaw in the skip_onboarding method’s failure to validate the return value of check_login_and_get_user. Specifically:
- The check_login_and_get_user function returns either a WP_User object (on successful authentication) or a WP_REST_Response error object (on failure).
- The skip_onboarding method does not check whether the return value is a valid WP_User object before passing the user_id to authenticate_and_redirect.
- As a result, even if authentication fails (e.g., due to an invalid login_nonce), the authenticate_and_redirect function is called with the attacker-supplied user_id, creating a valid authentication cookie.
This logic error effectively bypasses the 2FA mechanism, allowing attackers to authenticate as any user by specifying their user_id (e.g., 1 for the default admin).
Vulnerable Path
The plugin introduces a REST endpoint at:
This endpoint is intended to allow verified users to skip the onboarding screen after configuring 2FA. However, due to broken logic in the code flow, any unauthenticated request that supplies a valid user_id can trigger a login bypass.
- Skip Onboarding():
This method is responsible for handling the 2FA skip request and calling the internal authentication logic. It accepts parameters like user_id, login_nonce, and redirect_to.
It calls check_login_and_get_user() like this:
The issue:
- It does not check if $user is a valid WP_user object.
- Even if the login fails or the nonce is incorrect, the method blindly continues to log the user in.
- check_login_and_get_user() - Correctly Detects Failure, But Not Enforced:
This function checks if the nonce is valid and fetches the user:
- This method returns a WP_REST_Response (error object) if the login nonce is invalid.
- But this error value is not handled properly in the calling function.
- authenticate_and_redirect() Assumes User is Verified:
This method sets the authentication cookie and redirects the user to the provided URL:
This method assumes the user is authenticated, but in this case, it’s being called even when the previous check failed. Since the user_id is still passed to it (even if invalid), it creates a session for that user regardless of authentication status.
Code Flow Summary
- A POST request to /wp-json/really-simple-ssl/v1/two-fa/skip_onboarding is received with user_id, login_nonce, and redirect_to.
- skip_onboarding calls check_login_and_get_user to validate the nonce and retrieve the user.
- If the nonce is invalid, check_login_and_get_user returns a WP_REST_Response error, but skip_onboarding ignores this and proceeds.
- skip_onboarding calls authenticate_and_redirect with the unverified user_id, which sets a session cookie and redirects the user, effectively granting access.
Exploitation
Step 1: Access your locally hosted target application at: http://localhost:8080/wp-admin

You’ll be presented with the default WordPress login screen, ”indicating the admin panel is protected”.
Step 2: Run the Exploit Script. We will use the following Python script to exploit the vulnerable REST API endpoint. The script targets the /reallysimplessl/v1/two_fa/skip_onboarding route, which is insecurely implemented.
Use the script below as exploit.py: https://github.com/enciphers-team/cve-exploits/blob/main/CVE-2024-10924.py
Run the script:
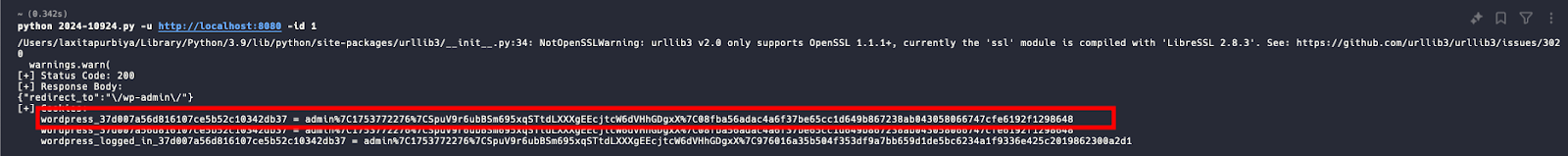
- -u specifies the target URL.
- -id is the user ID to impersonate (1 is usually the admin).
If successful, you will receive a 200 OK response along with authenticated session cookies
Step 3: Now that we have valid cookies, we can inject them into the browser to log in as admin on the WordPress site.
Open Firefox and go to: http://localhost:8080/wp-admin → Press F12 or right-click → Inspect to open Developer Tools.
Go to the Storage tab → expand Cookies → select http://localhost:8080.

Click the “+” button to add a new cookie.
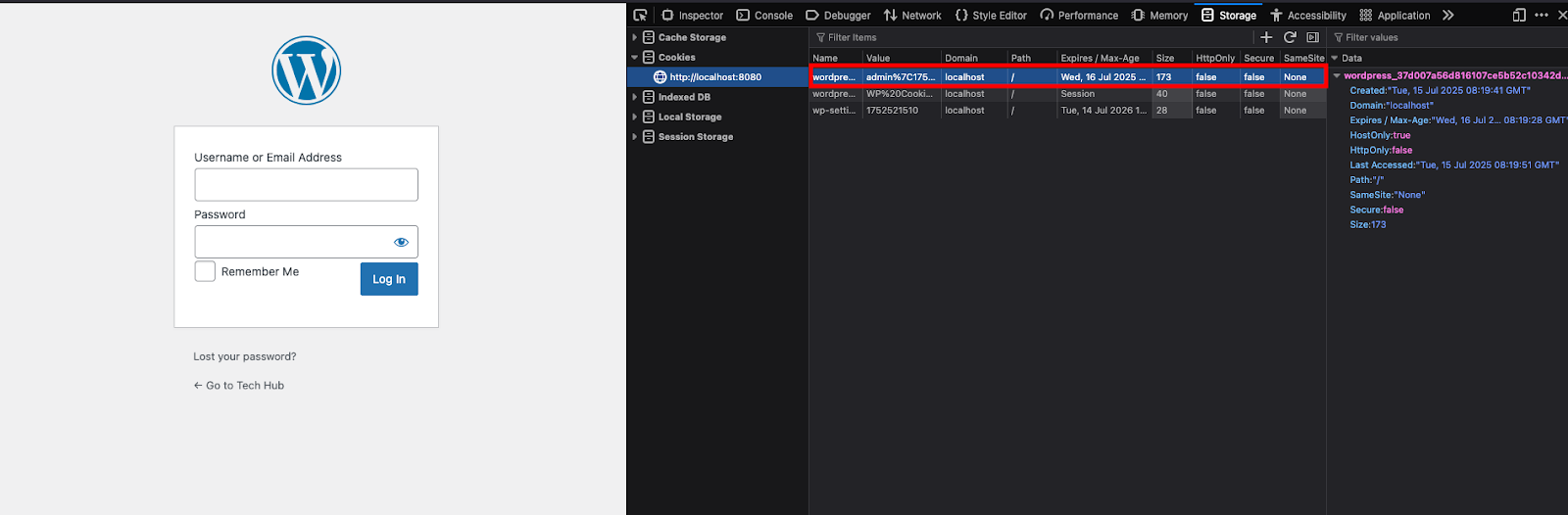
Add the cookies retrieved from the exploit script, each cookie requires:
- Name: e.g., wordpress_logged_in_...
- Value: from the script output
Close the Developer Tools tab.
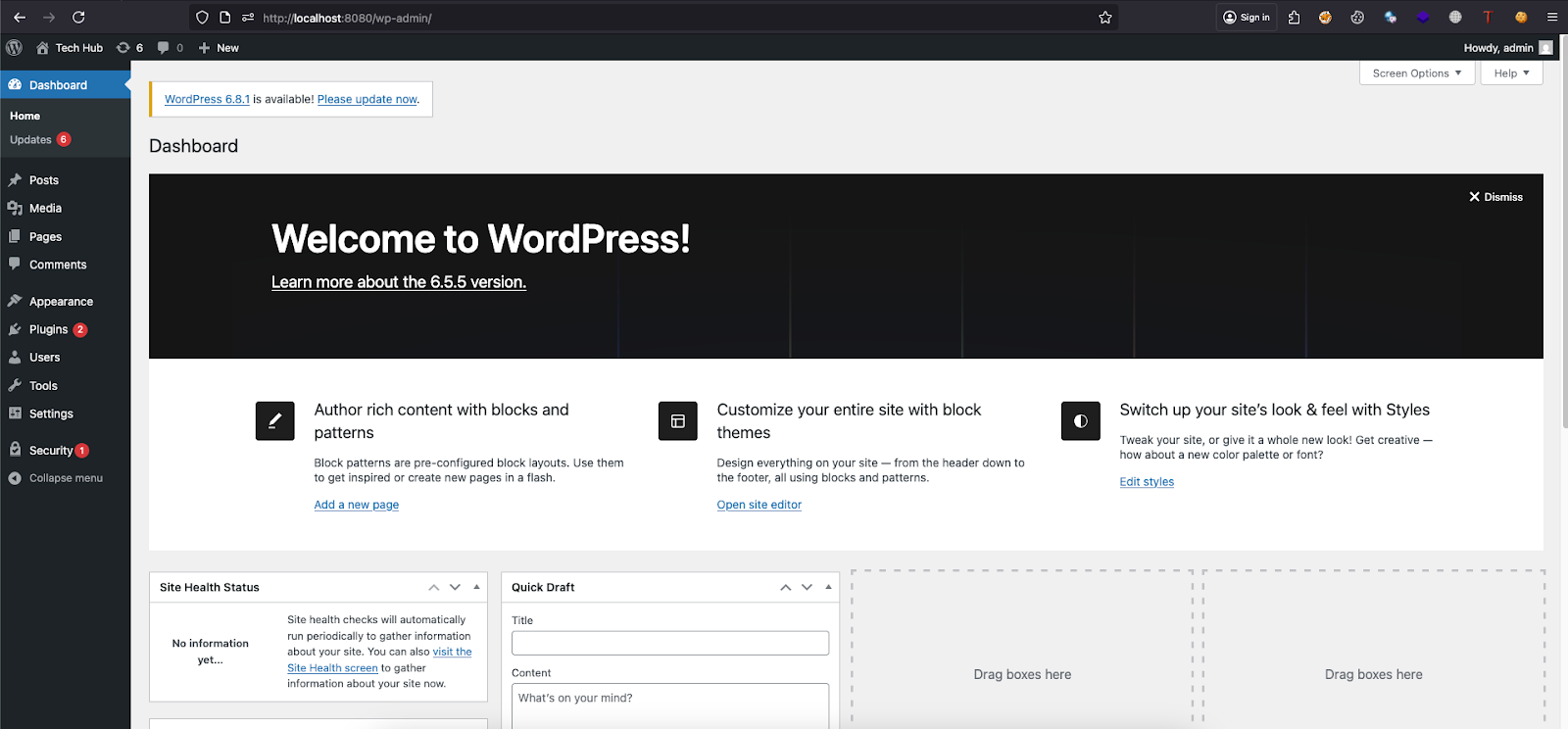
Refresh the page. If you added the cookies correctly, you’ll be logged in directly as the admin.
Mitigation Steps
To protect your WordPress site from CVE-2024-10924, take the following actions immediately:
- Update the Plugin: Upgrade Really Simple Security (Free, Pro, or Pro Multisite) to version 9.1.2 or later, which patches this vulnerability. Check your WordPress admin panel for updates or download the latest version from the official plugin repository.
- Disable 2FA Temporarily (if unable to update): If immediate updating is not feasible, disable the 2FA feature in the plugin settings. Be aware that this reduces security, so prioritize updating as soon as possible.
References
https://www.wiz.io/vulnerability-database/cve/cve-2024-10924








.png)




