Overview:
Grav, a file-based web platform known for its simplicity and flexibility, has a security vulnerability identified as CVE-2024-34082. This vulnerability affects versions prior to 1.7.46 and allows low-privileged users with page edit permissions to read any server files using Twig syntax.
This vulnerability arises from Grav's improper handling of Twig syntax, which permits low-privileged users to access sensitive server files. Among these files are the Grav user account files located at /grav/user/accounts/*.yaml. These files contain hashed user passwords, two-factor authentication (2FA) secrets, and password reset tokens.
- CVE Identifier: CVE-2024-34082
- CVSS Score: 8.5
- Affected Versions: Prior to 1.7.46
Technical Analysis:
CVE-2024-34082 is a critical vulnerability in Grav CMS versions prior to 1.7.46 that allows low-privileged users with page edit permissions to read arbitrary files on the server. This issue arises from how Grav handles Twig, its PHP templating engine, and exposes sensitive files through improper configuration.
Understanding the Vulnerability
Grav CMS uses Twig to render dynamic content, allowing users with site.edit permissions to include Twig code in page content. In versions before 1.7.46, a specific Twig function, read_file, enables reading any file accessible to the web server’s user (e.g., www-data in Apache setups). Without proper restrictions, this function becomes a security risk.
For example, a user could add the following Twig code to a page:
In a vulnerable Grav version, this code retrieves the contents of the specified file, such as user account data or server configurations, if the web server has read access. Why does this issue occur? Grav stores sensitive information, like hashed passwords and two-factor authentication (2FA) secrets, in YAML files within the web root. These files are readable by the web server, making them vulnerable to unauthorized access through Twig.
Root Cause in Vulnerable Versions
The vulnerability arises from several design flaws in Grav’s implementation prior to 1.7.46:
- Unrestricted Twig Functions: Grav’s Twig integration includes the read_file function, which can access any file the web server user has permission to read. Vulnerable versions lack a sandbox to restrict this function, allowing users to embed it in page content without validation.
- Inadequate Input Validation: Users with site.edit permissions can add Twig code via the admin interface. Grav fails to filter dangerous functions like read_file, enabling unsafe code execution.
- Exposure of Sensitive Files: Grav’s file-based architecture stores user data in YAML files within the web root, accessible to the web server user. This design makes sensitive information easy to retrieve if Twig functions are not restricted.
- Weak Permission Controls: The site.edit permission, often granted to content editors, allows modifying page content, including Twig templates. Vulnerable versions do not distinguish between safe and unsafe Twig usage, permitting risky operations.
These flaws allow users with minimal privileges to access sensitive files, potentially exposing critical data or system information.
How It Was Fixed
In Grav 1.7.46, the developers implemented stricter Twig sandboxing to restrict functions like read_file, preventing arbitrary file access. They also added validation to ensure only safe Twig code is executed, even by users with site.edit permissions. This update eliminates the ability to read sensitive files through page content.
The issue highlights the risks of combining powerful templating functions with insufficient validation in a file-based CMS. By failing to restrict Twig’s capabilities and protect sensitive files, Grav versions prior to 1.7.46 allowed unauthorized access to critical data.
Exploitation:
Now let’s explore the exploitation scenario for CVE-2024-34082. With a low-privileged user account that has page-editing permissions, they can access sensitive system files like /etc/passwd, /etc/shadow, or any other by crafting a simple page in the admin panel. We’ll outline the steps and provide Proof of Concept (PoC) examples to show how this works.
How an Attacker Can Exploit
To pull this off, an attacker needs a low-privileged user account with site.edit permissions. They might start by logging into the normal user login panel at http://target:port/login, which is the standard endpoint for user access. But to exploit this vulnerability, they need to find and log into the Grav admin panel. Here’s a challenge: try discovering the admin login panel yourself!
Once logged into the admin panel with the low-privileged account, the attacker can create a page to embed malicious Twig code that uses the read_file function. This function allows them to read any file the web server (e.g., www-data on Apache) has permission to access. Let’s see this in action with two PoCs.
- Accessing /etc/passwd
The attacker navigates to the page creation section in the admin panel and creates a new page, naming it something like “exploit.” In the page content, they add this Twig code:
This code attempts to read the /etc/passwd file, which lists user accounts on the server. After saving the page, they visit http://target:port/exploit. If the vulnerability is present, the page displays the file’s contents, such as:
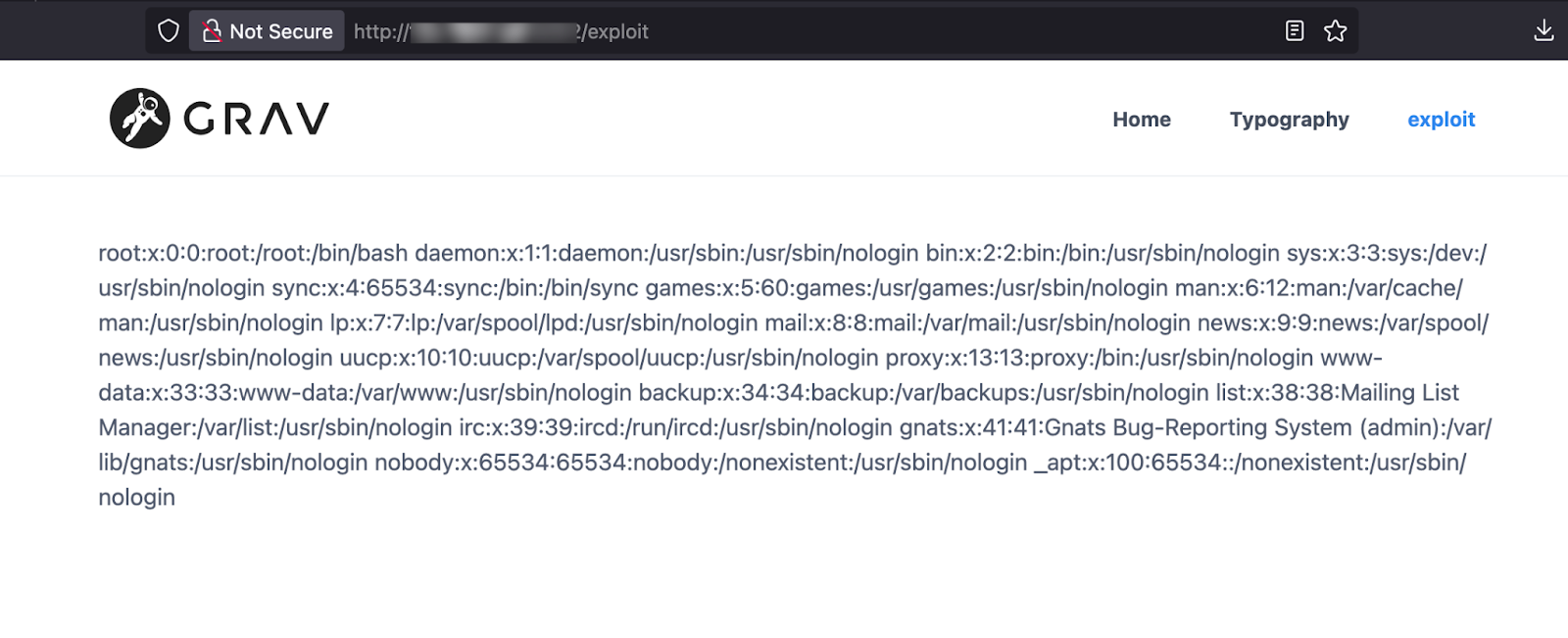
This exposes the server’s user list, which could help the attacker map out the system for further attacks.
- Targeting /etc/hosts
For a more target, the attacker can try reading the /etc/hosts file, which contains local hostname-to-IP address mappings. While this file does not typically store sensitive credentials, it can reveal internal network configurations, custom host entries, or indicators of internal services that may not be publicly exposed. They add this Twig code to the “exploit” page:
After saving and accessing http://target:port/exploit, the page might reveal
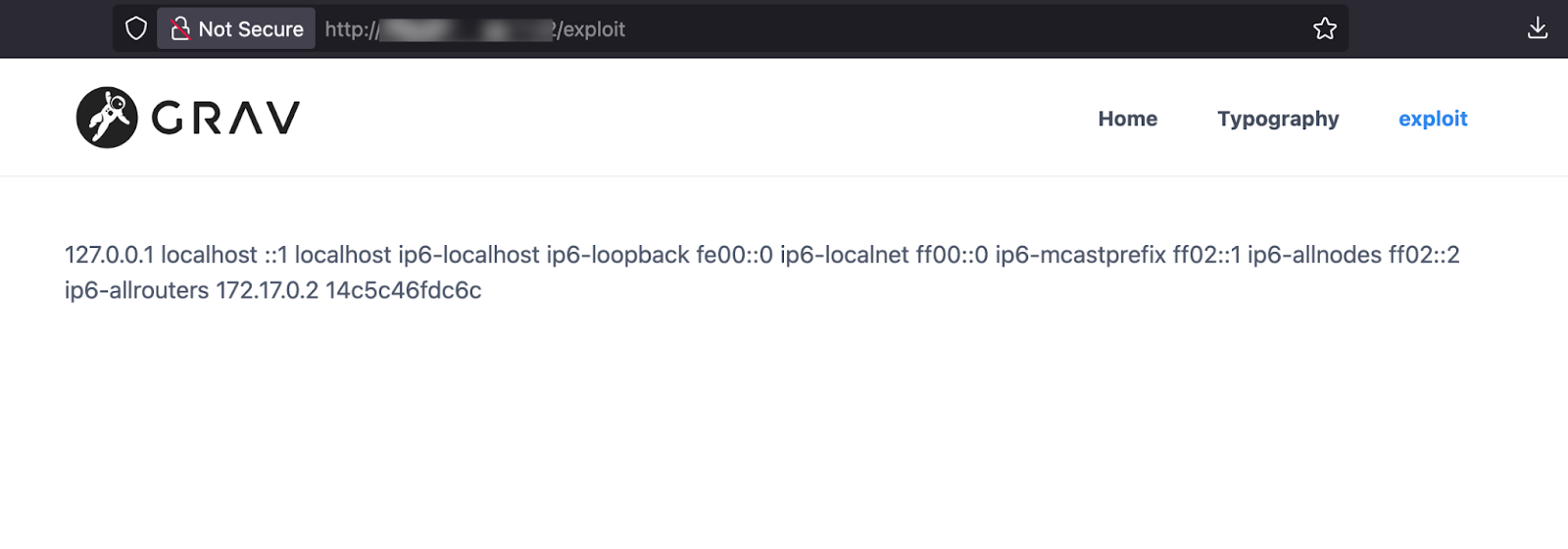
This exposes local hostname-to-IP address mappings. Note that /etc/shadow access depends on the web server’s permissions and may not always be possible.
Attackers can even escalate this technique further. By systematically exploring readable files, they may uncover configuration data or user account information that includes hashed credentials. If any of these hashes belong to privileged users, such as administrators, the attacker could attempt to crack them offline. Successfully recovering an admin password would allow full access to the admin panel, enabling complete site compromise.
Impact
The ability to read arbitrary files on the server allows attackers to:
- Hijack user accounts, including those with administrative privileges, by accessing hashed passwords and password reset tokens.
- Access sensitive configuration files and potentially other critical files on the server.
Recommendations:
- Upgrade to 1.7.46: Immediately update Grav to the latest version to mitigate the risk.
- Review User Permissions: Carefully assess the permissions granted to users, ensuring that only trusted individuals have access to sensitive functions.
- Monitor for Suspicious Activity: Be vigilant for any unusual activity on your website, such as unauthorized changes to content or user accounts.
References :
https://securityonline.info/cve-2024-34082-grav-cms-vulnerability-opens-door-to-account-takeovers/
https://vulners.com/cvelist/CVELIST:CVE-2024-34082
https://secalerts.co/vulnerability/CVE-2024-34082







.png)





