Summary
In the evolving world of web development, where server-side rendering and component architectures are key, a major security flaw in React Server Components (RSC) has put millions of applications at risk of remote code execution (RCE). On December 3, 2025, independent researchers disclosed CVE-2025-55182, affecting React's RSC implementation. This also impacts frameworks like Next.js (originally tracked as CVE-2025-66478).
- Severity: CVSS v4.0 Score: 10.0 (Critical) – Allows unauthenticated RCE via a single HTTP request.
- Affected Components: React 19.x (react-server-dom-* packages), Next.js 15.x/16.x App Router, and RSC-enabled bundlers like Vite, Parcel, and Waku.
- Exploitability: Deterministic and requires no user interaction; affects default production setups without custom code.
- Prevalence: According to Wiz Research, 39% of scanned cloud environments are vulnerable, with 44% exposing public Next.js endpoints.
- Mitigation: Upgrade immediately to React 19.0.1+ and Next.js 15.0.5+. No effective workarounds are available.
This analysis dives into the vulnerability's mechanics, detection methods, and wider implications for the JavaScript ecosystem. It draws from reverse-engineered exploits, protocol details, testing across runtimes (Node.js, Bun, and Deno), and insights from researchers like Lachlan Davidson. Nicknamed "React2Shell" by the community, this deserialization issue had already attracted exploitation attempts by state-linked actors shortly after disclosure.
Architectural Foundations: React Server Components and the Flight Protocol
React Server Components (RSC), introduced in React 19 after experiments in 18.x, shift rendering logic to the server. Components run only on the server, streaming serialized data to the client for hydration. Benefits include:
- Keeping server secrets (e.g., API keys, database queries) hidden from the client.
- Reducing client-side JavaScript size for better performance in data-intensive apps.
The core technology is the Flight Protocol, a binary-over-HTTP serialization format for RSC payloads. It's not JSON but a chunked, reference-based stream for efficient incremental rendering:
- Chunks: Basic units like strings, numbers, objects, arrays, or symbols, indexed (e.g., Chunk 0, Chunk 1).
- References: Symbols such as $0 (for Chunk 0), $1:prop (property of Chunk 1), or $@0 (module-scoped Chunk 0). These compress data by avoiding duplicates.
- Blobs: Binary data via $B0 (Blob 0), e.g., for images.
- Transmission: Via HTTP/2+ streams or POSTs, often as multipart/form-data or JSON to endpoints like /_rsc (Next.js) or /api/actions.
Decoding happens in bundler-specific packages:
- react-server-dom-webpack@19.x (for Webpack/Next.js).
- react-server-dom-parcel@19.x (for Parcel).
- react-server-dom-turbopack@19.x (for Turbopack in Next.js).
Example of Reference Mechanism:
Decodes to: { object: 'fruit', name: 'cherry' }.
This efficient structure lacks proper safety in vulnerable versions, allowing exploits through unchecked property traversal.
Deep Technical Analysis of CVE-2025-55182
The vulnerability enables RCE by exploiting deserialization in React Server Functions (RSF) via the Flight Protocol. It stems from weak reference resolution during decoding, letting attackers access the JavaScript Function constructor and run arbitrary code before any validation.
2.1 React Server Functions and Flight Protocol Basics
RSF serializes arguments into chunks sent to the server. Chunks reference each other with symbols like $1 or $1:prop.
2.2 Root Cause: Unrestricted Property Resolution via Prototypes
In older vulnerable versions, a crafted reference could traverse the prototype chain all the way to the object’s constructor and then its parent constructor because no ownership checks (like hasOwnProperty) were done. This chain ultimately exposed the Function constructor to attackers.
Example Payload:

2.3 Using Thenables for Execution
Next.js awaits decoding results. If an object's then property points to the Function constructor, it's invoked during await.
Example:
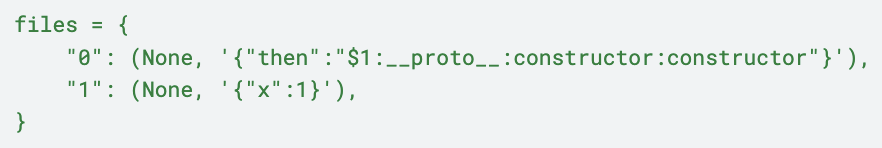
2.4 Self-Referential Chunks with $@ Operator
The $@ operator returns raw chunks, enabling self-references:
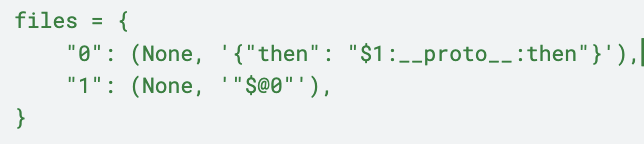
This overrides .then with React's internal handler, leading to a second decoding pass.
With status: "resolved_model", it enters initializeModelChunk, parsing attacker-controlled values.
2.5 Final Exploit: Code Execution via $B Blobs
Attackers control chunk properties to hijack blob resolution:
- Set _prefix to malicious code.
- Set _formData.get to the Function constructor.
Crafted Payload Example:

Executes: Function("process.mainModule.require('child_process').execSync('calc');")().
This happens before action validation, even with invalid headers.
Remediation Roadmap
6.1 Primary Fixes: Patching
- React: Update to react-server-dom-webpack@19.2.1.
- Next.js: Use npx next@latest or pin to 16.0.7+.
- New Features: Strict resolvers, schema validation, safe mode on errors.
6.2 Interim Defenses
- WAF Rules: Block large POSTs or match rogue patterns (e.g., /\xFF.{10,}/ or /$@.*resolved_model/).
- Disable Endpoints: Remove experimental: { serverComponents: true } in next.config.js (may break features).
- Runtime Hardening: Use Node's --disallow-code-generation (affects legitimate code).
- Cloud Protections: Providers like Vercel, Netlify, AWS deployed filters by Dec 4, 2025; scan with Akamai or Kaspersky.
Conclusion
A simple multipart POST to a default Next.js or React 19 app could trigger RCE without custom code, authentication, or validation. This highlights risks in seamless server-client integrations.
The teams patched quickly (within 48 hours), and providers added filters. However, with React's ubiquity, many apps remain vulnerable as of December 5, 2025.
Immediate Actions:
- Upgrade to React 19.0.1+ / Next.js 15.0.5+ / 16.0.7+ if using RSC or App Router.
- If patching isn't immediate, secure RSC endpoints with WAFs.
- Monitor for active exploits.
References :
https://nextjs.org/blog/CVE-2025-66478
https://github.com/assetnote/react2shell-scanner













